Hardware accessory giant Logitech has confirmed it suffered a data breach in a cyberattack claimed by the Clop extortion gang, which conducted Oracle E-Business Suite data theft attacks in July.
Logitech International S.A. is a Swiss multinational electronics company that sells hardware and software solutions, including computer peripherals, gaming, video collaboration, music, and smart home products.
Today, Logitech filed a Form 8-K with the U.S. Securities and Exchange Commission, confirming that data was stolen in a breach.
“Logitech International S.A. (“Logitech”) recently experienced a cybersecurity incident relating to the exfiltration of data. The cybersecurity incident has not impacted Logitech’s products, business operations or manufacturing,” disclosed Logitech.
“Upon detecting the incident, Logitech promptly took steps to investigate and respond to the incident with the assistance of leading external cybersecurity firms.”
Logitech says the data likely includes limited information about employees and consumers, as well as data relating to customers and suppliers, but the company does not believe hackers gained access to sensitive information such as national ID numbers or credit card information, as that data was not stored in the breached systems.
Logitech says that the breach occurred through a third-party zero-day vulnerability that was patched as soon as a fix was available.
This statement comes after the Clop extortion gang added Logitech to its data-leak extortion site last week, leaking almost 1.8 TB of data allegedly stolen from the company.
While the company does not name the software vendor, the breach was likely caused by an Oracle zero-day vulnerability exploited by the Clop extortion gang in July data-theft attacks.
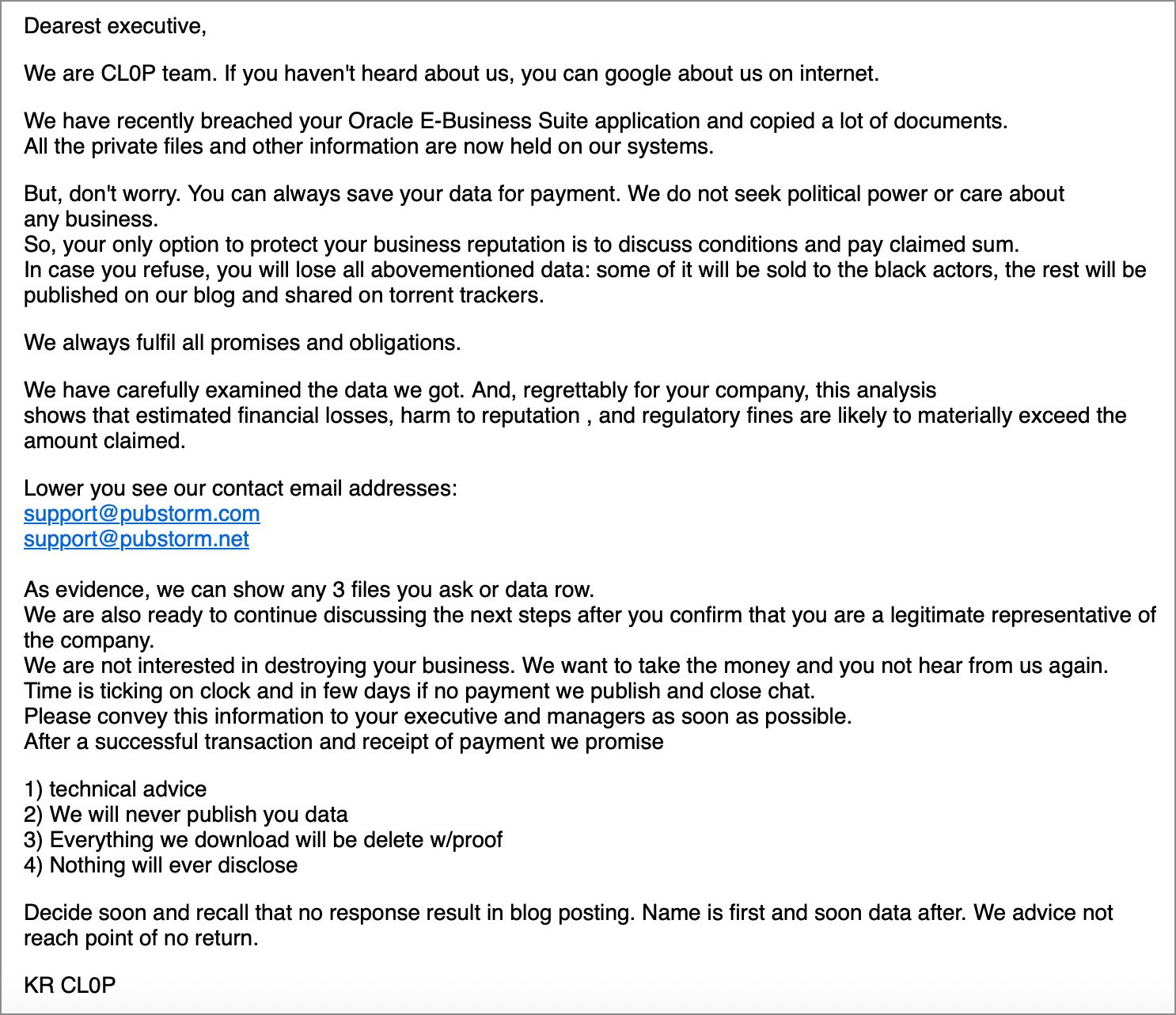
Last month, Mandiant and Google began tracking a new extortion campaign in which numerous companies received emails from the Clop ransomware operation claiming that sensitive data had been stolen from their Oracle E-Business Suite systems.
These emails warned that the stolen data would be leaked if a ransom demand was not paid.
Soon after, Oracle confirmed a new E-Business Suite zero-day, tracked as CVE-2025-61882, and issued an emergency update to fix the flaw.
The Clop extortion gang has a long history of exploiting zero-day flaws in massive data theft attacks, including:
- 2020: Exploited a zero-day in the Accellion FTA platform, affecting nearly 100 organizations.
- 2021: Exploited a zero-day in SolarWinds Serv-U FTP software.
- 2023: Exploited a zero-day in the GoAnywhere MFT platform, breaching over 100 companies.
- 2023: Exploited a zero-day in MOVEit Transfer, which was Clop’s most extensive campaign to date, where the attackers stole data from 2,773 organizations worldwide.
- 2024: Exploited two Cleo file transfer zero-days (CVE-2024-50623 and CVE-2024-55956) to steal data and extort companies.
Other organizations impacted by the 2025 Oracle E-Business Suite data theft attacks include Harvard, Envoy Air, and The Washington Post.
BleepingComputer contacted Logitech earlier this month and again today with questions regarding the breach and will update the story if we receive a response.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.


